Eventlog to Firewall: Difference between revisions
(Created page with "=Intro= Sometimes it is annoying to see that people try tog into your terminalserver with bad credentials doing this all day long to find a valid user and password combination...") |
|||
| (4 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
=Intro= | =Intro= | ||
Sometimes it is annoying to see that people try | Sometimes it is annoying to see that people try to logon into your terminalserver with bad account credentials, they try to do this all day long to find a valid user and password combination in the hope that the guessed account is valid. | ||
this all day long to find a valid user and password combination. | |||
This is like a burglar in front of your | This is like a burglar in front of your door, trying one key pair after the other with no one interrupting him. | ||
That's why we came up with evt2fw, we search the eventlog for intruders and block them on our local firewall. | That's why we came up with evt2fw, we search the eventlog for intruders and block them on our local firewall. | ||
Eventlog to Firewall is a tool to prevent hackers to get into your system. | Eventlog to Firewall is a tool to prevent hackers to get into your system. | ||
It runs on Windows and looks into the Eventlog and searches invalid logons due to wrong | It runs on Windows and looks into the Eventlog and it searches invalid logons due to wrong access credentials, if it finds them then block it for a certain amount of time. | ||
Eventlog to Firewall is a script called '''evt2fw'''. it is designed to run on Windows2008 Terminalservers. | Eventlog to Firewall is a script called '''evt2fw'''. it is designed to run on Windows2008 Terminalservers. | ||
<br> | <br> | ||
=Features= | =Features= | ||
*Add unauthorized users / ip addresses to the local Windows Firewall | *Add unauthorized users / ip addresses to the local Windows Firewall | ||
| Line 184: | Line 184: | ||
|style="width:10%; vertical-align: top;"| | |style="width:10%; vertical-align: top;"| | ||
'''Download the script'''<br> | '''Download the script'''<br> | ||
[[File:Download.png|60px|link= | [[File:Download.png|60px|link=https://coolscript.org/download/scripts/evt2fw.zip|Download]] | ||
<br> | <br> | ||
|style="width:90%; vertical-align: top;"| | |style="width:90%; vertical-align: top;"| | ||
Latest revision as of 13:09, 4 March 2022
Intro
Sometimes it is annoying to see that people try to logon into your terminalserver with bad account credentials, they try to do this all day long to find a valid user and password combination in the hope that the guessed account is valid.
This is like a burglar in front of your door, trying one key pair after the other with no one interrupting him.
That's why we came up with evt2fw, we search the eventlog for intruders and block them on our local firewall.
Eventlog to Firewall is a tool to prevent hackers to get into your system. It runs on Windows and looks into the Eventlog and it searches invalid logons due to wrong access credentials, if it finds them then block it for a certain amount of time. Eventlog to Firewall is a script called evt2fw. it is designed to run on Windows2008 Terminalservers.
Features
- Add unauthorized users / ip addresses to the local Windows Firewall
- Remove ip addresses after a specified time from the local Windows Firewall
- Logging of logon and logoff requests to syslog
System Requirements
- Windows 2008 (32/62)
- RDP/Terminalserver enabled
- Windows Firewall enabled and properly configured
- Active State Perl
- A scheduled task to run the script
Windows Firewall
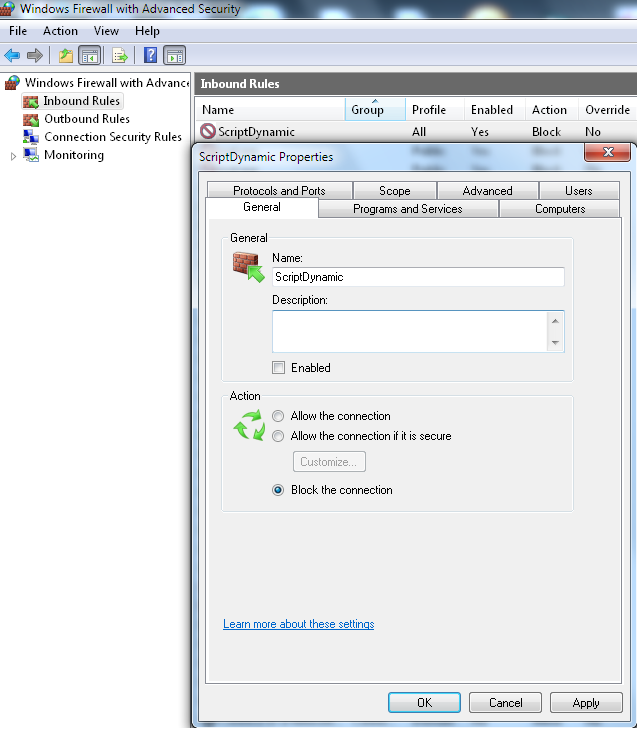
- Add a new rule and name it of your choice
- Please don't enable the rule, the script is managing this by itself.
- Set Block as Action
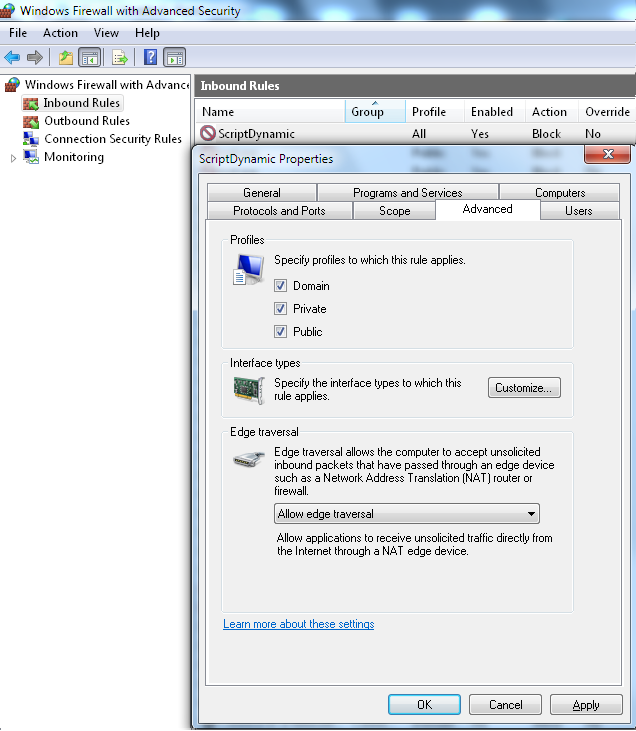
- Set all Profiles for this rule
- Allow edge traversal
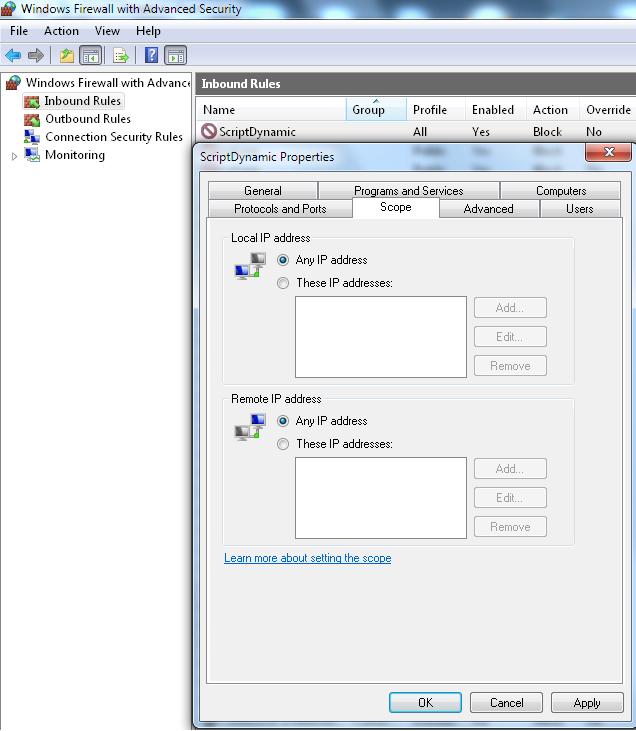
- Nothing needs to be added in Scope but you can check this later for blocked IPs by the script
Script Files
| File | Purpose |
|---|---|
| evt2fw.pl | The Perl Script |
| evt2fw.xml | The Script Configuration |
| evt2fw.dat | Internal Database (CSV), this is where we hold our data |
| evt2fw.sta | Status File, this is where we save the last execution time |
Configuration
- Configuration of evt2fw.xml
- XML Version: <?xml version="1.0"?>
- Root Element: <Config>
| Element | Attribute | Array | Purpose |
|---|---|---|---|
| Setup | TimeBack | No | Integer value to specify the time which the script should check behind the current time. By default this value is set to 0 or is remarked out. We use the last given time in fw2fw.sta to get the time setting automatically. |
| BlockTimeDelta | No | Integer value to define the time delta in seconds to check for intruders Example: 86400 will check the last 24 hours for intruders | |
| ExpireDelta | No | Integer value to define the time delta in seconds. This is to specify for how long we keep the ip address of the intruder blocked | |
| MaxRequest | No | Amount of requests or login attemos which a intruder can send before we block the ip | |
| FirewallRuleName | No | The Name of the Windows Firewall Rule | |
| UseGMT | No | The Terminalserver uses UTC for the eventlog. Set this value to 1 to calculate a GMT offset for the time behind | |
| IgnoreSystemWhitelist | No | The default is 0, we will whitelist private ip addresses anytime, this is making sure
that you don't lock out yourself. | |
| Logage | No | Amount of days before we delete our logfiles | |
| Syslog | IP | Yes | IP of Syslog Server |
| Whitelist | IP | Yes | Whitlist Ip address, no wildcard or CIDR format but you may set parts of the IP, Example: IP="192.168" would whitelist all addresses beginning with 192.168 (the first two octets) |
Example Configuration
- Check behind 24 hours for intruders
- Keep intruders blocked for 24 hours
- Max 3 login attemps using bad passwords
- use GMT offset calculation
- Whitelist private ip addresses
- Write Log
- Use SyslogServer 192.168.100.1/2
- Whitelist 213.10
<?xml version="1.0"?>
<CONFIG>
<Setup
BlockTimeDelta="86400"
ExpireDelta="86400"
MaxRequest="3"
FirewallRuleName="Script-Dynamic"
UseGMT="1"
IgnoreSystemWhitleist="0"
Syslog="1"
/>
<Syslog IP="192.168.100.1"/>
<Syslog IP="192.168.100.2"/>
<Whitelist IP="213.10"/>
</CONFIG>
Syslog
evt2fw can send data via UDP to a syslog server, we will use parsing friendly key value pairs.
| Field | Description |
|---|---|
| SRV | Server name from where the script runs |
| M | The modus, set S2F (Syslog 2 Firewall) |
| LFR | Local Firewall Rule Name, in our sample it is 'ScriptDynamic' |
| LOF | Logoff User |
| LOU | Logon User (will be zero in case of a intrusion) |
| WID | (0/1) Whitelisted Intrusion Detection |
| DIP | Detected IP |
| IDU | Intrusion Detected User (will be zero in case of a secussful logon) |
| TGE | Time generated (WMI Timestamp) |
Script Internals
evt2fw is checking the following IDs from the Eventlog
- 4624 - Logon Type 10 - Successfull login
- 4625 - Logon Type 10 - Bad Login attemp
- 4647 - Logoff event
Message parsing
- Source Network Address
- Logon Type
- Account Name
WMI Query:
("Select * from Win32_NTLogEvent Where Logfile = 'Security' and (eventcode = '4625' or eventcode = '4624' or eventcode = '4647') and TimeGenerated > TimegivenFromScrip
|
|